Proof of Process - The unsung hero set to come of age
- Home /
- Blog Posts /
- Proof of Process - The unsung hero set to come of age
- Nick Vermeulen
- Privacy , PoP
- 5 September 2025 · Updated 5 September 2025 · 4 min read
Table Of Contents
Beyond the Hype: Why “Proof of Process” is the Unsung Hero of Trust
In the buzzing world of blockchain and decentralized systems, “Proof of Work” (PoW) often steals the spotlight. We hear about its energy consumption, its role in securing Bitcoin, and its fundamental importance in achieving consensus. But what if I told you there’s another “proof” that, while less glamorous, is arguably just as, if not more, critical to building real-world trust and efficiency?
Enter Proof of Process (PoP).
While not as widely adopted a term as PoW, the concept behind Proof of Process is gaining traction, particularly as we look to apply blockchain and distributed ledger technologies beyond simple cryptocurrency transactions. PoP isn’t about solving complex cryptographic puzzles; it’s about verifying the integrity, sequence, and authenticity of every step within a workflow or operation.
What Exactly is Proof of Process?
Imagine a complex supply chain, a multi-stage manufacturing process, or even a detailed legal procedure. In each of these scenarios, countless actions occur, documents are exchanged, and decisions are made. Historically, verifying that each step happened correctly, in the right order, and without tampering has been a monumental challenge. It often relies on manual checks, auditing, and a significant degree of trust in intermediaries.
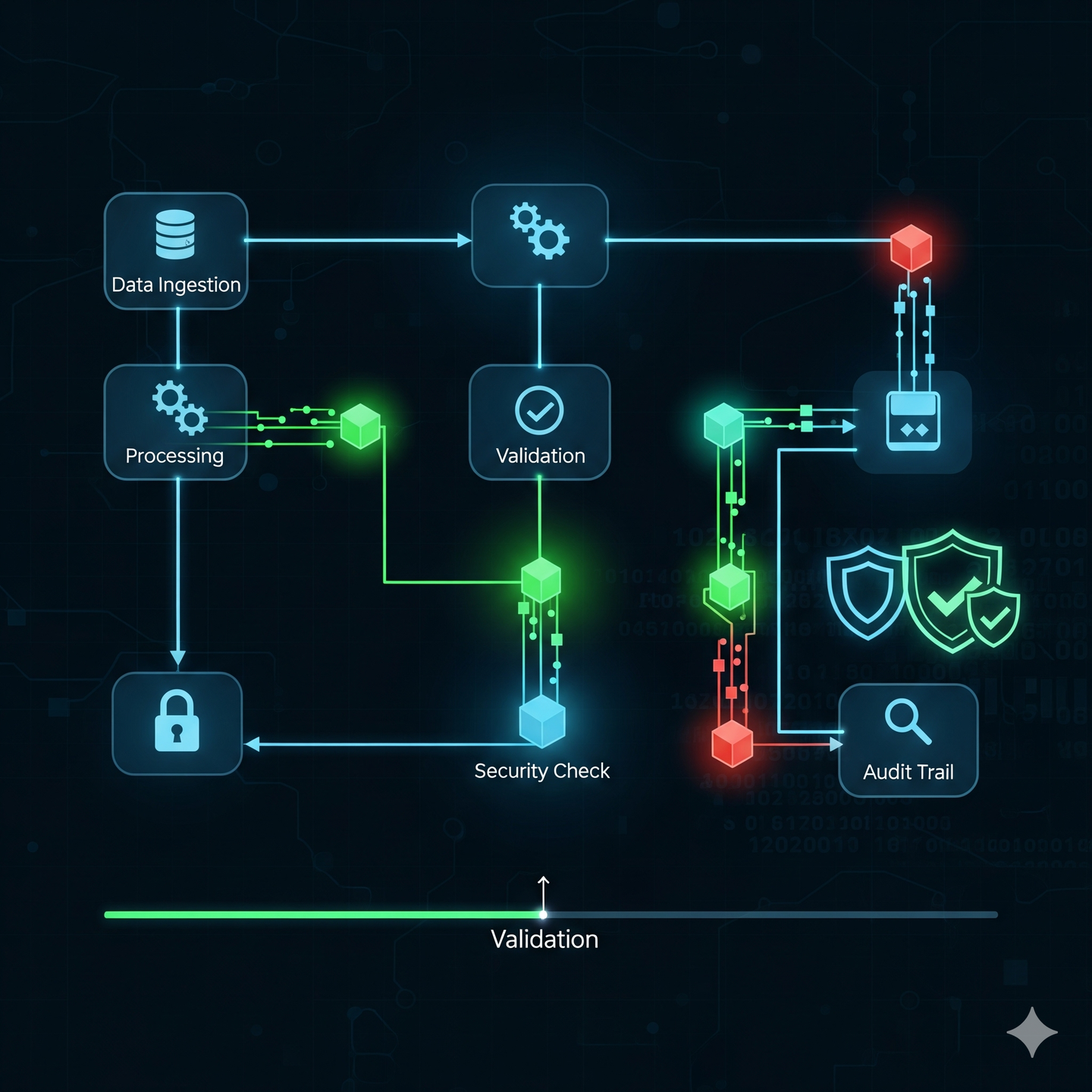
Proof of Process, especially when powered by blockchain or DLT, offers a revolutionary alternative. It leverages cryptographic principles to create an immutable, verifiable record of every action, data input, and state change within a defined process.
Here’s how it works:
- Atomic Steps: Each distinct action or decision within a process is treated as an “atomic” step.
- Cryptographic Fingerprints: As each step is completed, it’s digitally signed, hashed, and timestamped. This creates a unique, unalterable cryptographic “fingerprint.”
- Chained Records: These fingerprints are then linked together, often in a cryptographic chain, making it impossible to alter a previous step without invalidating all subsequent ones.
- Verifiable Logic: Smart contracts can enforce the rules and logic of the process, ensuring that only valid transitions between steps are allowed.
Why PoP Matters: Beyond Just “Work”
While Proof of Work secures the network itself, Proof of Process secures the actions that happen on that network and in the real world. Here’s why it’s so incredibly important:
- Unprecedented Transparency: No more “black boxes.” Every participant, with appropriate permissions, can see exactly how a process unfolded, from start to finish. This is invaluable in sectors like regulatory compliance, financial auditing, and ethical sourcing.
- Enhanced Accountability: When every action leaves an immutable trace, accountability skyrockets. It becomes clear who did what, when, and how. This deters fraud, errors, and malicious activities.
- Reduced Disputes: With a verifiable record of every step, disagreements over what happened or when it happened can be quickly resolved by consulting the PoP.
- Streamlined Auditing: Audits, which can be time-consuming and expensive, become far more efficient. Auditors can quickly verify compliance and identify discrepancies.
- Increased Trust in Complex Systems: In an increasingly interconnected world, processes often span multiple organizations and jurisdictions. PoP builds trust without relying on any single central authority. Think about global supply chains, where proving the origin and journey of a product is paramount.
- Automation with Confidence: When you have verifiable proof of process completion, you can automate subsequent actions with far greater confidence, knowing that all prerequisites have been met.
Real-World Applications
The potential applications of Proof of Process are vast:
- Supply Chain Management: Track goods from raw material to consumer, verifying every hand-off, quality check, and environmental condition.
- Regulatory Compliance: Provide irrefutable proof that all necessary steps and checks were followed for permits, approvals, or data handling.
- Healthcare: Securely record patient journeys, ensuring proper protocols were followed in treatments and drug dispensing.
- Manufacturing: Verify every stage of assembly, quality control, and testing for complex products.
- Legal Processes: Document the lifecycle of legal documents, ensuring proper signatures, filings, and notifications.
The Future is Process-Driven
While Proof of Work remains foundational for many decentralized networks, it’s merely the engine that keeps the train running. Proof of Process is about verifying the journey of the train, the cargo it carries, and the stops it makes along the way.
As industries increasingly embrace digitalization and look to blockchain for more than just speculative assets, the demand for robust, verifiable processes will only grow. Understanding and implementing “Proof of Process” will be key to unlocking true efficiency, trust, and innovation in the digital age. It’s time to shift our focus and recognize this unsung hero for the critical role it plays in building a more transparent and accountable future.


