Proof of Process - Self-Sovereign Identity
- Home /
- Blog Posts /
- Proof of Process - Self-Sovereign Identity
- Nick Vermeulen
- Privacy , PoP , Identity
- 5 September 2025 · Updated 5 September 2025 · 4 min read
Table Of Contents
Your Digital Fingerprint: How “Proof of Process” Can Revolutionize Self-Sovereign Identity
In our increasingly digital world, proving who you are online is a constant, cumbersome battle. We hand over sensitive documents, answer security questions, and rely on centralized authorities to verify our identities – often leading to fragmented data, privacy concerns, and vulnerability to breaches. But what if there was a way to “self-prove” your identity, without constantly exposing your personal data?
Enter Proof of Process (PoP), the unsung hero that could unlock the true potential of Self-Sovereign Identity (SSI).
The Problem with Current Identity Verification
Think about how you prove your identity today:
- Sharing sensitive documents: Every time you sign up for a new service, you likely upload scans of your driver’s licence, passport, or utility bills. This data then sits on various company servers, creating multiple points of failure for your privacy.
- Centralized databases: Many identity systems rely on a central authority (government, bank, etc.) to store and verify your information. This creates a single point of attack for hackers and gives that authority immense power over your digital self.
- Lack of granular control: You either prove your full identity or nothing at all. What if you just need to prove you’re over 18, or that you live in a certain country, without revealing your exact age or address?
This fragmented, exposed, and often inefficient system is ripe for disruption.
Proof of Process Meets Self-Sovereign Identity
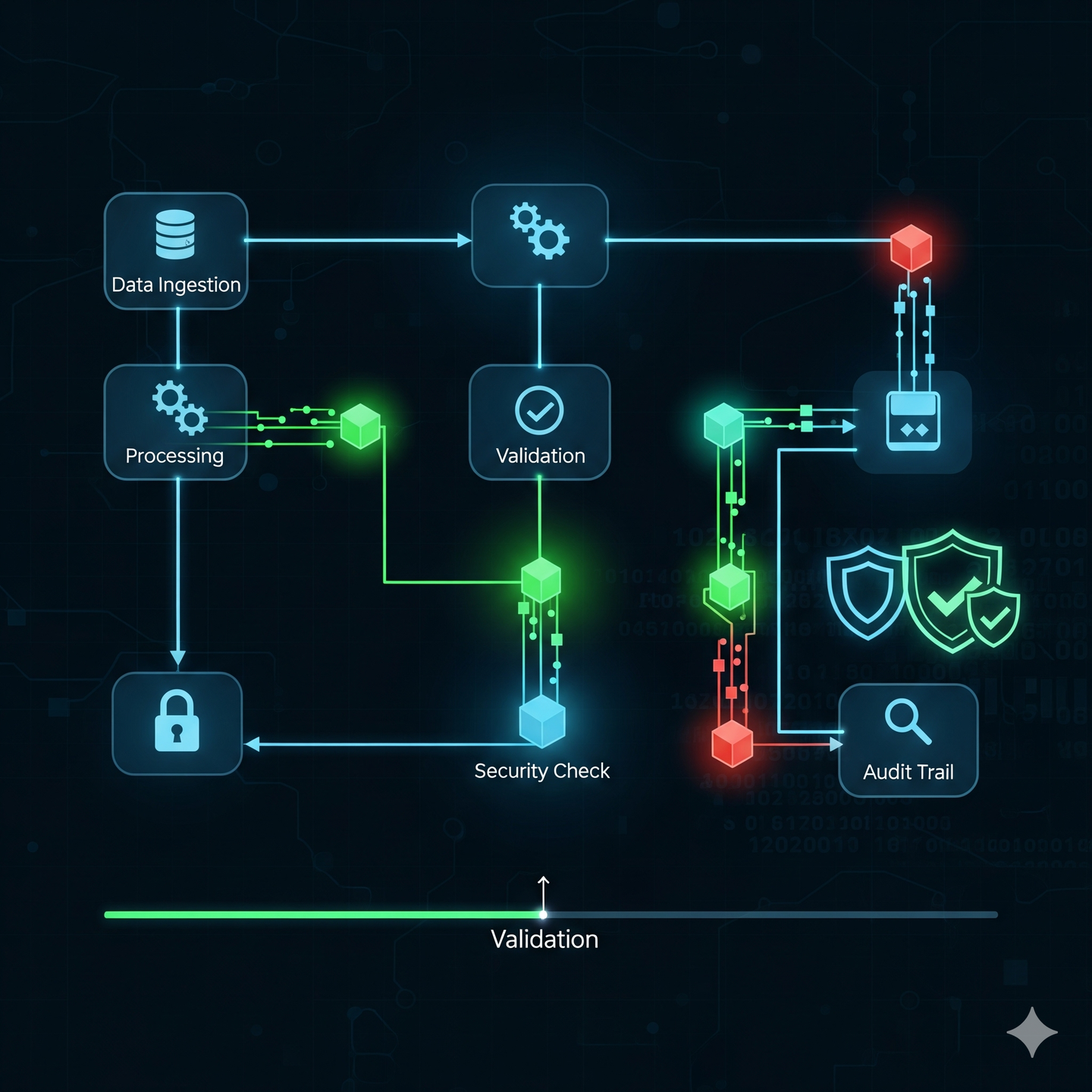
Self-Sovereign Identity (SSI) is a model where an individual has complete control over their digital identity. Instead of relying on third parties to manage your data, you own and manage your own verifiable credentials. PoP takes this a critical step further by providing a robust, cryptographically verifiable way to generate and maintain those credentials.
Here’s how Proof of Process can empower self-proving identity:
-
Verifiable Credential Issuance:
- Imagine a government agency issuing you a digital driver’s licence. With PoP, theprocess of issuing that licence – from your initial application to the final digital signature – can be recorded on a distributed ledger.
- This isn’t about storing your personal data on the blockchain, but rather creating an immutable “proof of process” that the credential was legitimately issued by the authorised entity, to you, following all required steps.
- You receive a cryptographically signed “Verifiable Credential” (VC) that proves you have a valid licence.
-
Attestation of Attributes, Not Raw Data:
- When you need to prove a specific attribute (e.g., “I am over 18”), you don’t send a copy of your driver’s licence. Instead, you present your VC.
- A PoP system allows you to generate a zero-knowledge proof (ZKP) based on your VC. This ZKP cryptographically proves the attribute (“over 18”) without revealing your date of birth or any other personal details. The recipient can then independently verify that this proof is linked to a legitimately issued credential (via the PoP record).
-
Immutable Event Log of Identity Lifecycle:
- Every significant event related to your identity – issuance of a new credential, revocation of an old one, an update to an attribute – can be recorded as a PoP.
- This creates an unalterable audit trail of your identity’s lifecycle, providing transparency and preventing unauthorised changes. If a credential is ever challenged, the PoP can demonstrate its legitimate origin and journey.
-
Granular Consent and Control:
- Because you hold the PoP-backed credentials, you control when and to whom you present them, and what specific information you reveal from them.
- The “proof of process” ensures the integrity of the credential itself, giving relying parties confidence that what you’re presenting is authentic, even if they’re only seeing a minimal subset of your data.
The Benefits of Self-Proving Identity with PoP
- Enhanced Privacy: You share only the absolute minimum information required, reducing your digital footprint and exposure.
- Improved Security: Your identity is no longer dependent on centralized honeypots of data. Even if a credential issuer’s database is breached, your core identity on a PoP-secured SSI system remains intact and verifiable.
- Fraud Reduction: The cryptographic immutability of PoP makes it incredibly difficult to forge credentials or impersonate individuals.
- User Empowerment: You become the steward of your own digital identity, deciding who sees what and when.
- Streamlined Verification: Imagine instantly proving your age to an online retailer or your professional qualifications to a potential employer, all with a quick, secure, and privacy-preserving digital interaction.
The Road Ahead
While the full vision of PoP-enabled SSI is still evolving, the foundational technologies are here. As we move towards a more decentralized and privacy-conscious internet, the ability to self-prove your identity through cryptographically secured processes will not just be a convenience – it will be a fundamental right and a cornerstone of digital trust.
No more handing over your life story for every online interaction. With Proof of Process and Self-Sovereign Identity, your digital fingerprint becomes truly yours, managed by you, and verifiable by anyone, without compromising your privacy.