
A high‑level, non‑technical look at Self‑Sovereign Identity and the EU Digital Identity Wallet
Embracing Self-Sovereign Identity: A Promising Future for Personal Data Management If you live in the Channel Islands and want your sensitive data kept securely on your own devices, new digital identity tools can help. Self‑sovereign identity (SSI) is a simple idea: you hold your own digital credentials (like an ID card, proof of age, or a qualification) in a secure app and share only what’s needed, with your consent.
Read more
A detailed look into SSI and the current projects including the EU Data Wallet
Navigating the Evolving Landscape of Self-Sovereign Identity: From Failures to Future Promises TL;DR Self-sovereign identity (SSI) is advancing but fragmented: Sovrin’s shutdown in 2025 underscores funding and adoption woes, while standards like AnonCreds (zero-knowledge proofs ZKPs for deep privacy) and SD‑JWT (lightweight web disclosure) compete. Projects like cheqd.io, Dock, and ION drive innovation, but interoperability lags. The EU’s EUDI Wallet, rolling out by 2026 with pilots testing cross-border creds, could unify implementations in one user‑controlled app—enabling seamless, consent‑based data sharing and digital sovereignty.
Read more
A high level look into SSI and the current projects including the EU Data Wallet
Why this post Self-sovereign identity (SSI) and its adjacent ecosystems evolved fast over the last 24 months. This post summarises where the core standards sit, how the European Digital Identity (EUDI) Wallet programme frames the stack, and what’s actually shipping across networks and vendors—using current, primary sources throughout. This post is a bit more technical in nature as implementation gets closer. If you need more details or background please read the deeper dive version of this post.
Read more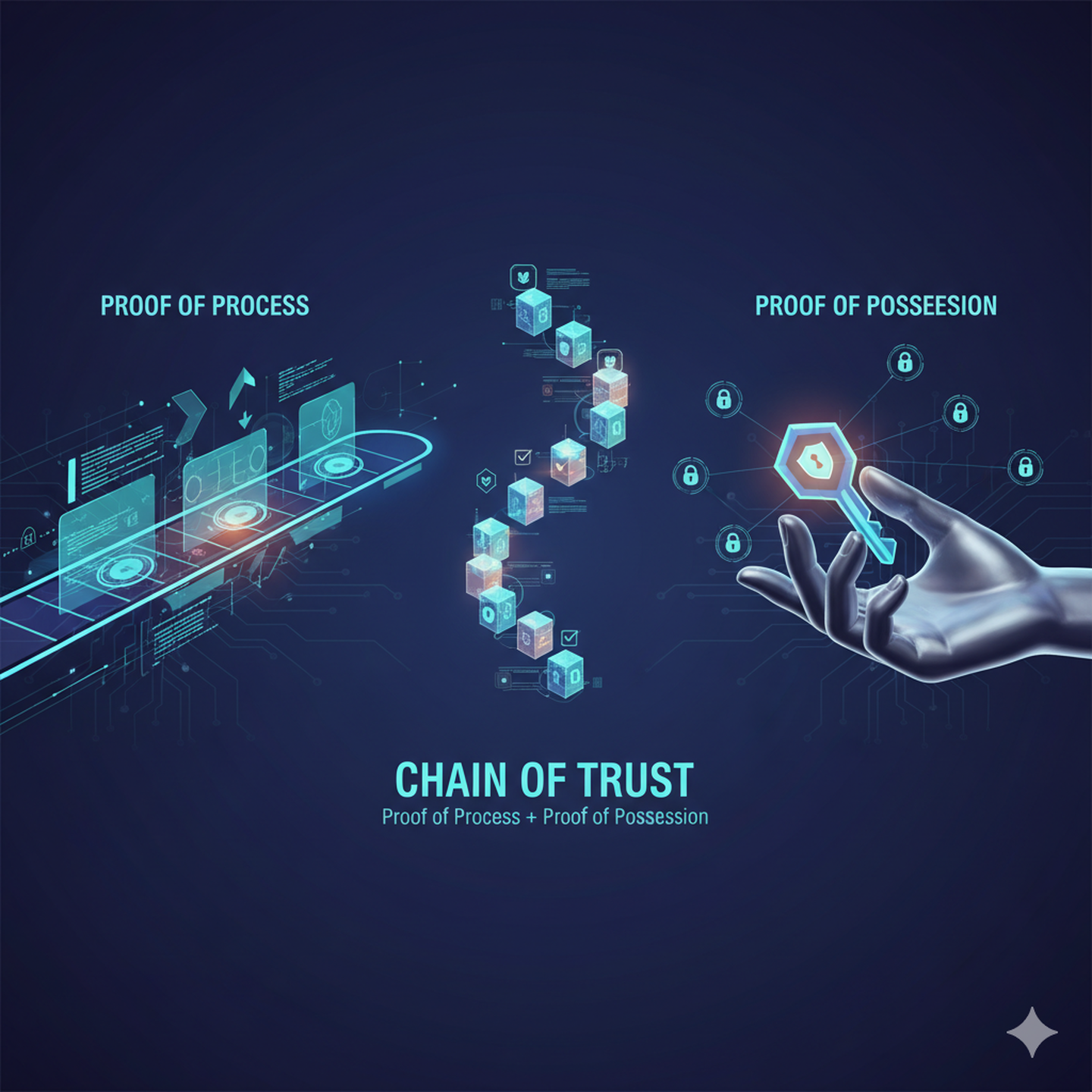
From Paper Trails to Digital Chains: How Proof of Process and Possession are Revolutionizing Trust
From Paper Trails to Digital Chains: How Proof of Process and Possession are Revolutionizing Trust In our increasingly digital world, the need for verifiable trust is more critical than ever. We’re constantly asking two fundamental questions: “What happened?” and “Who was responsible?” Answering these questions reliably and transparently is the key to creating secure, dependable systems.
Read more
Proof of Process - Self-Sovereign Identity
Your Digital Fingerprint: How “Proof of Process” Can Revolutionize Self-Sovereign Identity In our increasingly digital world, proving who you are online is a constant, cumbersome battle. We hand over sensitive documents, answer security questions, and rely on centralized authorities to verify our identities – often leading to fragmented data, privacy concerns, and vulnerability to breaches. But what if there was a way to “self-prove” your identity, without constantly exposing your personal data?
Read more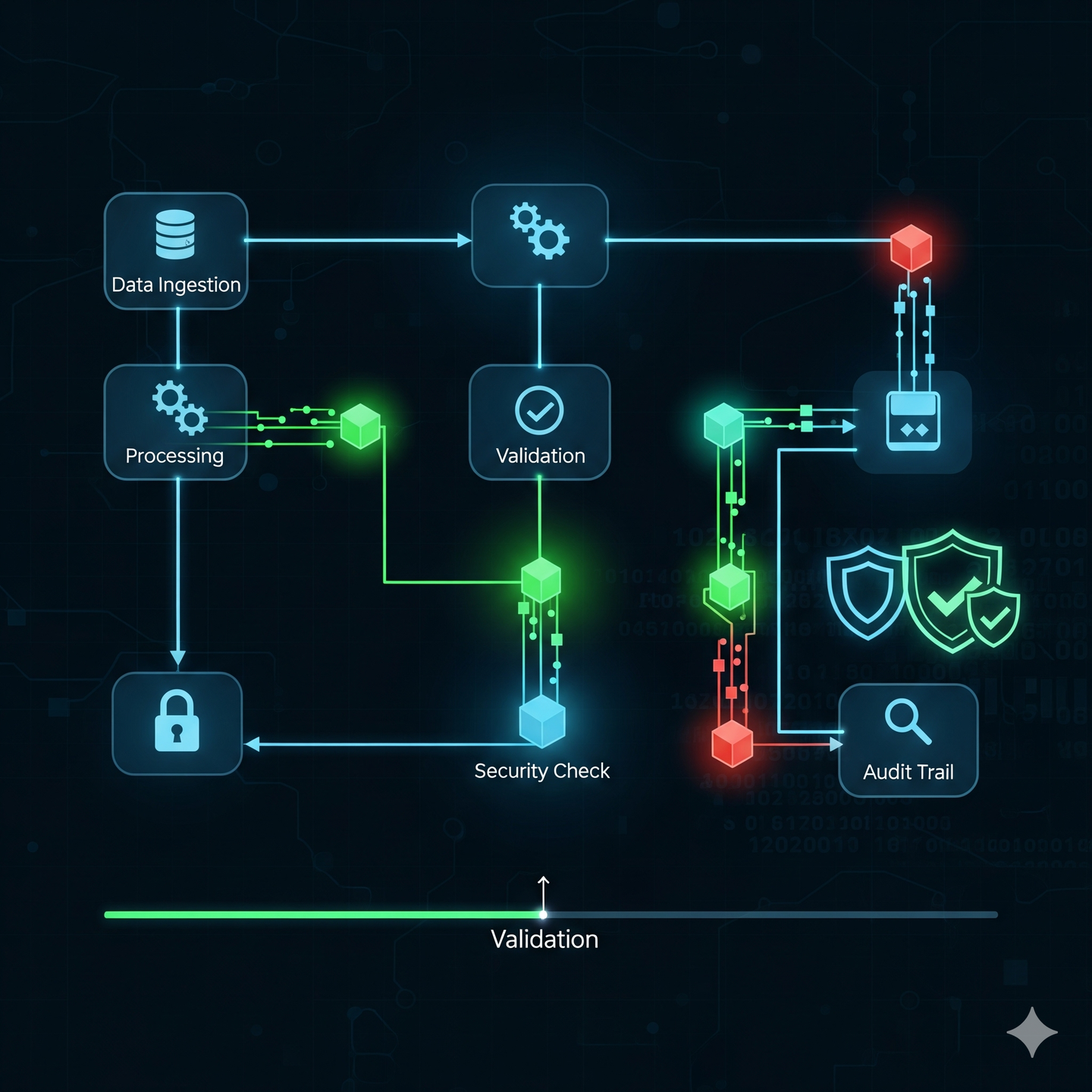
Proof of Process - The unsung hero set to come of age
Beyond the Hype: Why “Proof of Process” is the Unsung Hero of Trust In the buzzing world of blockchain and decentralized systems, “Proof of Work” (PoW) often steals the spotlight. We hear about its energy consumption, its role in securing Bitcoin, and its fundamental importance in achieving consensus. But what if I told you there’s another “proof” that, while less glamorous, is arguably just as, if not more, critical to building real-world trust and efficiency?
Read more
Privacy by Design - A look back and a look forward
From X.400 to SMTP: The Story of a Simpler Takeover In the early days of digital communication, there were two competing visions for email. One was the complex, feature-rich, and highly structured X.400 standard, championed by the International Telecommunication Union (ITU). The other was the simpler, more flexible Simple Mail Transfer Protocol (SMTP), which emerged from the internet’s open and collaborative development. Ultimately, SMTP and complementary protocols like PGP (Pretty Good Privacy) prevailed due to their simplicity, adaptability, and the decentralized nature of the internet.
Read more
Privacy by Design & the EU Data Wallet
From X.400 to SD-JWT: A Privacy Evolution in the EU Digital Identity Wallet The landscape of digital identity is constantly evolving, and with the advent of the EU Digital Identity (EUDI) Wallet, we’re seeing a significant leap towards user-centric and privacy-respecting systems. For those of us with a longer history in digital communication, the term “X.400” might ring a bell. While seemingly disparate, comparing the foundational concepts behind X.400 and the modern SD-JWT (Selective Disclosure for JSON Web Tokens) within the context of the EUDI Wallet highlights a remarkable evolution, particularly in how we handle and control personal data.
Read more
Privacy by Design Comes to the fore
Enhancing Privacy and Security in Messaging with SD-JWT In a world where our digital conversations are the new frontier of personal data, the security and privacy of our messaging applications are more critical than ever. We’ve all grown accustomed to end-to-end encryption, which is a great first step, but what happens when you need to share personal information within a conversation? SD-JWT (Selective Disclosure for JSON Web Tokens) offers a powerful solution that can take messaging privacy to a whole new level.
Read more